In the past when I was thinking about elevation of a user I always thought about elevating a member of the administrators group from a Medium Integrity Level to a High one.
But elevation is not only for administrators, it also works for any other user that gets a split security token at login time.
For example any members of the Power Users or Backup Operators groups, have a split-personality as well.
When normally logging on as such a user and run something as admin, the UAC prompt comes up:
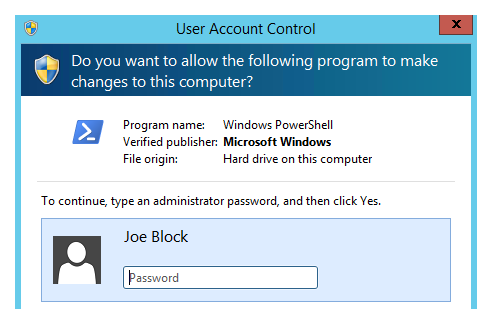
The wording here is actually incorrect, I don't have to type an administrator password, Joe Block is not an administrator, but his password gets me past the UAC prompt.
whoami /groups as a normal user:
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Power Users Alias S-1-5-32-547 Group used for deny only
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
We can see the Power Users group is not in effect: Group used for deny only, any action that requires this membership will fail.
whoami /groups as a elevated user:
Group Name Type SID Attributes
=========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Power Users Alias S-1-5-32-547 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
Now, elevated the second part of the split-token is in effect and we are a proper Power User
whoami /groups as elevated member of Backup Operators:
Group Name Type SID Attributes
==================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Desktop Users Alias S-1-5-32-555 Mandatory group, Enabled by default, Enabled group
BUILTIN\Backup Operators Alias S-1-5-32-551 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
The difference between the last two is that a backup operator gets a integery level of High while the power user only gets Medium Plus (what ever that means).
Now my question, sometimes I need to run an elevated process for such a user while a different (standard user) is logged on to Windows.
It is easy to start a non-elevated process. I can use the (Shift+)context menu to Run as different user, use runas.exe or PowerShell:
start-process -verb runas powershell.exe
only shows me real administrators in the UAC prompt.
I tried other elevation tools, but they all bring up the same UAC prompt.
Even the following doesn't work:
$someCredentials = Get-Credential
Start-Process powershell -Credential $someCredentials -ArgumentList '-noprofile -command &{Start-Process powershell.exe -verb runas}'
I still get a UAC prompt without the non-admin account I want to use.
My UAC level is: Default - Always notify me when: (slider at the top) and I don't want to change that.
The only solution I found so far, only works if I already have an elevated administrator PowerShell running, then I can use:
psexec.exe -u USERNAME -p PASSWORD -d -h -i -accepteula $env:SystemRoot\System32\WindowsPowerShell\v1.0\powershell.exe
I'm using psexec, which has the -h switch meaning: run the process with the account's elevated token, if available.
I also have to specify the username and the password for the account.
I think elevating a user should be possible without the help of an administrator but I don't know how. psexec.exe gives me Access Denied if I run it as a non-admin.